Categories: General
Date: Jan 25, 2017
Title: Ransomware
Ramsomware, the new and evolving cyber threat
I am often asked to differentiate between ransomware, malware and virus infections. End users are expectant of their anti virus solutions to protect them against an ever evolving smorgasbord of nasties, developed by a wide spectrum of equally nasty folk out there. Some want to make a buck, others want to brag to their peers, and for a small minority, it’s the technical challenge that drives them.
Ransomware is a sophisticated piece of malware that blocks the victim’s access to his/her files.
There are three types of ransomware
- The most common infection is Encrypting ransomware, which blocks system files and demand payment to provide the victim with the key that (may) can decrypt the blocked content. Examples include Cryptolocker, Locky, Cryptowall, and the many evolved variants
- Locker ransomware, locks the victim out of the operating system, but does not encrypt files. The attackers still ask for a ransom to unlock the infected computer. Examples include Winlocker.
- The third type is the Master Boot Record (MBR) ransomware. When MBR ransomware strikes, the boot process can’t complete as usual, and prompts a ransom note to be displayed on the screen. Examples include Satana and Petya ransomware.
I will concentrate on the first type, as it is the most common and the most damaging. Ransomware has some key characteristics that set it apart from other malware:
- It features unbreakable encryption, which means that you can’t decrypt the files on your own, unless your daddy is Seymour Cray, and he has a couple of spare Petaflops available for you to cruise on.
- Does not care if your files are your holiday snaps, or your company financials, or all the illegally downloaded music you have saved up for years…it will encrypt all files.
- It can scramble your file names, so you can’t know which data was affected.
- One of the variants even adds a different extension to your files
- After encrypting all your files, it will display an image or a message that lets you know your data has been encrypted and that you have to pay a specific sum of money to get it back.
- It requests payment in Bitcoins, untraceable and untrackable by cyber security researchers or law enforcements agencies.
- Tick Tock, the ransom payments has a time-limit. Going over the deadline typically means that the ransom will increase, but it can also mean that the data will be destroyed and lost forever.
- Ransomware often goes undetected by antivirus applications
- It often recruits the infected PCs into botnets, thus protection should be network wide.
- It can spread to other PCs connected in a local network, creating further damage;
- Ransomware can extract data from the affected computer (usernames, passwords, email addresses, etc.) and send it to a server controlled by cyber criminals
- Often the ransom note will be translated into the victim’s language, to increase the chances for the ransom to be paid.
As ransomware evolves and multiplies, you need to understand that you need at least baseline protection to avoid data loss and other troubles. In terms of platforms and devices, ransomware doesn’t discriminate either. PC’s Servers and even mobile devices are being specifically targeted.
So, how do ransomware threats spread?
These are the most common methods of getting infected
- Spam email campaigns that contain malicious links or attachments
- Security exploits in vulnerable software
- Internet traffic redirects to malicious websites
- Legitimate websites that have malicious links and code in their web pages
- Malvertising campaigns
- SMS messages (applies to phone devices only)
- PC to PC propagation
- Ransomware-as-a-service (RAAS)
These attacks get more refined by the day, as cyber criminals tweak their malicious code to be more intrusive and better suited to avoid the barriers we put in place. That is why each new ransomware variant is a bit different from its forerunner. So, by the time you get this “happy” message, its too late……
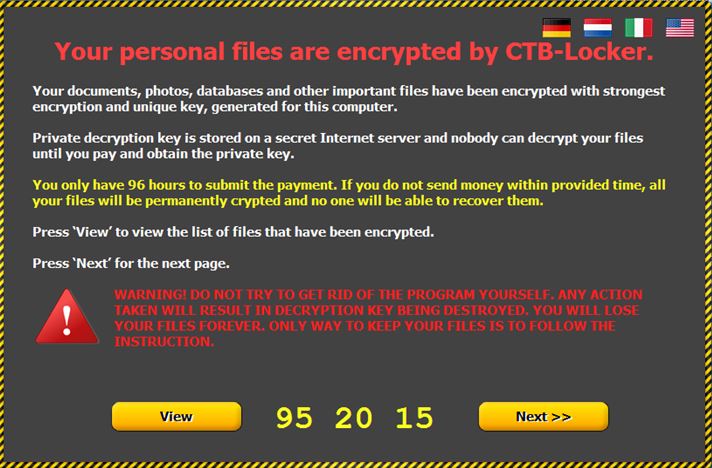
“But I have antivirus! Why didn’t it protect me from this” is the usual cry
Ransomware employs evasion tactics that ensure that its is:
- Not get picked up by antivirus products
- Not get discovered by cyber security researchers
- Not get observed by law enforcement agencies and their own malware researchers.
Think about it, the longer a malware stays unnoticed, the more data it can extract and the more damage it can do. The programmer does this by use of
- Encrypted Communication, thus difficult to detect in network traffic.
- Uses TOR and Bitcoin to avoid tracking by law enforcement agencies and to receive ransom payments.
- It uses anti-sandboxing mechanisms so that antivirus won’t pick it up.
- It employs domain shadowing to hide in. This is a method whereby they “add” a subdomain, hide it, and use the “front facing” domain to create legitimacy.
- Fast Flux, is a similar technique, using compromised domains to act as proxies.
- Encrypted payloads make it more difficult for antivirus to see that they include malware, so the infection has more time to unfold.
- Ransomware mutates, thus making tracking more difficult.
- Lie and hide in place, like an ambush predator, waiting for a trigger date, event or a specific system vulnerability.
Ten ways to reduce Ransomware attacks
- Backup your data regularly, include backup restore tests in your regime
- Patch software frequently, OS, Browser and identified application vectors
- Monitor and block suspicious traffic, manage outbound traffic
- Scan all downloads
- Scan all emails, make sure you have up to date endpoint AV installed
- Block EXE files, Windows Software Restriction Policies
- Disable “Hide extension file types”
- Disable macros through group policy
- Manage user privileges, use Admin logon sparingly, rather use a neutered user logon for day to day operations
- The most important point is, EDUCATE YOUR USERS, regularly
Need more information??
Please call or email me
Anton Schutte
027 524 9995
anton.schutte@selectit.co.nz

